Cyber And Intelligence
We support cybersecurity operations worldwide with leading-edge technical innovations, mission planning and automation solutions, cyber threat intelligence, and advanced cyber threat hunting and incident response. Our decades of experience and comprehensive offerings of technologies and tools enable a more secure and robust means to solve some of the toughest cyber challenges for our customers.
Explore Our Markets And Capabilities

Critical Infrastructure Protection (CIP): We support the industrial control systems (ICS) modernization strategy with a holistic system approach to streamline functionality, standardize components and architectures, and build in resiliency, redundancy, and security. We’re providing technical subject matter expertise in both compliance and functionality to support the ICS Program and Strategic Plans; providing standards review, commissioning support, compliance analysis, and network support.

Cybersecurity Assessments: We have deep domain expertise in securing weapon systems, space systems, and NC3 systems; providing sensor collection, in-depth vulnerability and SCP assessments, visualizing, and data streamlining to understand the cybersecurity posture of our customers’ networks and systems.

Rapid Prototyping Software Development: We’re working side-by-side with operators and analysts to develop force-multiplying quick reaction capabilities for successful operations and analytic development.

Rapid Turn Hardware Development And Manufacturing: We are a pioneer in the development and production of high resolution, high complexity printed electronics components for the DoD.

Reverse Engineering And Vulnerability Research: Our reverse engineers and vulnerability researchers have extensive experience in deciphering binary code and finding and developing exploits.

Embedded Software Engineering: We’re designing, developing, deploying, and maintaining capabilities to support computer network operations, with a focus on VR/RE/ED and collection capabilities.

Data Science: We have expertise in understanding data collection, tagging, transformation, routing and aggregation in order to visualize and provide access to data in a way that meets the needs of our end users.

Defensive Cyber Engineering: We’re designing, implementing, and sustaining capabilities to support defensive cyber operations, from collection and dataflow, to analysis and data visualization.

Internal Research And Development (IRAD): We believe innovation is the process of solving meaningful problems through an environment that empowers employees to think differently, rewards creativity, embraces boldness, and creates efficiency by breaking down internal stovepipes and getting to yes.
Contact Us
Get in touch with our cyber and intelligence and national security experts today.
Request InfoInnovation At Work
We believe innovation is the process of solving meaningful problems through an environment that empowers employees to think differently, rewards creativity, and embraces boldness to create efficiencies for effective customer solutions.
Leveling Up Your Cyber Skills – A Guide To Capture The Flag (Part 1)
There are a lot of factors to consider when you think about what type of Cyber Capture the Flag (CTF) you want to run. In addition to its type, you’ll have to decide on its location, length, content focus, and skill-level target. I’m going to discuss these in a way that hopefully makes them easy to think about—and to make a decision on.
Read MoreWriting For Non-Technical Writers
Technical writing encompasses the process of transforming intricate information into easily understandable content through the use of reports, user manuals, technical solutions, and other mediums.
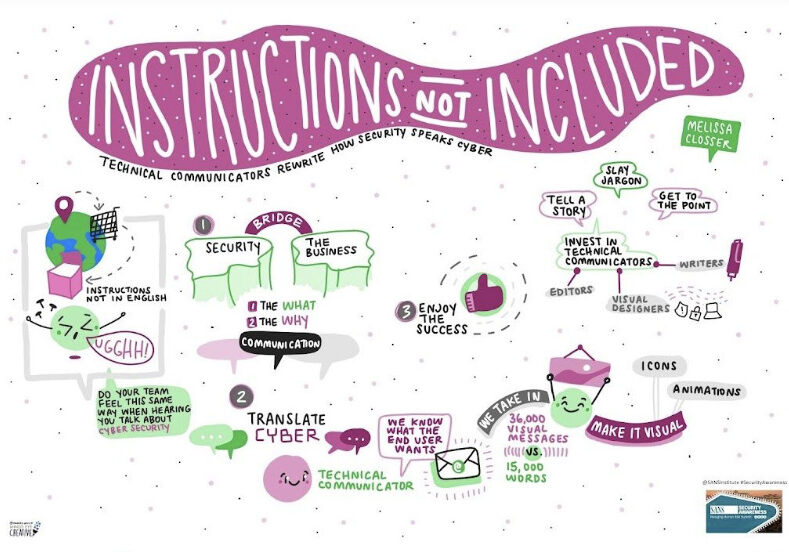
Read MoreRewriting How Security ‘Speaks Cyber’
With 82% of security breaches involving social attacks, errors, and misuse, our Business Information Security Office (BISO) knew a critical component to protecting our network is employee security communications, awareness, and education. I joined the BISO team to develop and lead BISO Outreach, working directly with employees to advocate for stronger security practices.
Read MoreImpactful Visualizations Through Data Integration
Much of our work within the Collection and Analytics Portfolio of National Security Solutions involves helping our customers get the most out of data. Sometimes this means helping architect solutions to acquire the specific data they want to work with our of a sea of information; and sometimes it means writing novel and highly specialized analytics to answer complex questions.
Read MoreCyber Solutions: Knowing History And Making History
To move forward, you sometimes must first look backward. For the engineers, technical writers, and scientists in Parsons Federal Solutions, research is the necessary key for success in the protection of our nation’s cyber security. Understanding where an organization has come from is inherent in helping to define its future. Many of the Parsons employees in the Federal Solutions directorate are contractors for the National Security Agency, Central Security Service (NSA/CSS).
Read More5 Ways Data Trends Will Change The Face Of The 2030s
As the “Roaring Twenties (Part Deux)” come to a close, this is the time of year where we guess the future tech mega-trends based on the current trajectory of the recent past. My goal in compiling the following list is to provide a mostly optimistic look at the anticipated innovative breakthroughs of the next decade.
Read MoreInspiring The Next Generation
Our team recently stepped up to show our love of STEM initiatives by taking part in the Technovation Girls Challenge as part of our Gives Back program. When we learned of the chance to be judges for this amazing initiative, our employees eagerly jumped in.
Read MoreThe Future Of Information Dominance
We provide technical and operational services and training and readiness solutions to public and private enterprises to discretely mitigate vulnerabilities derived from physical, technical, and criminal threats. Explore more from our director of training, Adam, about our training courses brought to you by our technical operations group to learn how you can best approach Publicly Available Information (PAI) and cultivate good research habits.
Read MoreProtecting Our Nation’s Infrastructure Cybersecurity
Over the last two decades, the rapid advancement of technology has presented challenges for cybersecurity. As the world becomes more and more interconnected, the frequency of major cyber-attacks has increased, and the impacts of these attacks have grown.
Read MoreNational Cybersecurity Awareness Month: Ransomware And What You Can Do To Prevent It
Every October, we participate in National Cybersecurity Awareness Month. Throughout the month, we stress the importance of cybersecurity overall and cybersecurity topics and best practices relevant to our employees and organization.
Read MoreWe Are A Connected Community Delivering Mission-Focused Cyber Solutions
Our people are our greatest asset. We strive to be an employer of choice that engages employees in the community and creates rewarding career paths to cultivate a resilient workforce that is ready for the future. The result is a thriving culture and a number of programs and initiatives specifically tailored to our team that we all can be proud of:








Employee Testimonials

Kena, CISSP, PMP, CSEP
National Security Solutions (NSS) Program Manager

Nicholas
Collection & Analytics VP, Parsons Fellow

Laura, PMP
Technical Director

Elizabeth
Technical Writer

Shawn
Lead Systems Engineer
Want To Work With Us? Join Our Cyber And Intelligence Team!
Systems Administrators
Our extensive experience in this field, combined with your knowledge, will propel your career forward with opportunity for advancement with top performance. We need our systems administrators to be versatile, enthusiastic to work in highly flexible, team-oriented environments and who have exceptional communication, analytical and organizational skills.
The Benefits Of Working With Us
General Benefits
- Medical, Dental, Pharmacy, and Vision (Coverage for Singles & Family)
- Parental Leave
- Flexible Work Arrangements
- Paid Time Off
- Wellness Program
- 401(k)
- Health Saving Account (HAS)
- Flexible Spending Account (FSA)
- Supplement Benefits for added coverages (Life Insurance & Financial)
Career Growth And Learning
- Internal mobility opportunities
- Early Career Professional Program
- Leadership & Management Programs
- Industry Conferences
- SME-led study groups
- In-house Technical boot camps
- Tuition and certification reimbursement
- In-house training series for employees: Propel for aspiring technical leaders and Cyber Analyst technical training series
Military Benefits
- Active, regular employees are eligible for up to 160 hours of paid leave for annual military training.
- Employees called to active duty are eligible for up to 60 months of paid leave differential for active duty.
- Paid transition time can be taken immediately upon return from active duty for up to 80 hours.
401k
- Annually, Parsons will contribute 100% on up to 8% of deferred compensation.
- Employees are immediately 100% vested in any company contributions Parsons makes to your account.
- Employee Stock Ownership Plan (ESOP) is also available to eligible employees.
Paid Time Off (PTO)
- Full-time (40 hours/week) employees with less than five years of service receive 160 hours of annual accrual PTO.
- Full-time (40 hours/week) employees with more than five years of Parsons service receive 200 hours of annual accrual PTO.
- PTO is accrued with each paycheck.
Employee Well-Being
- Participate in wellness activities to win prizes throughout the year.
- Earn discounts on health insurance premiums.
- Monthly wellness events such as Wellness Wednesday Coffee Talks, Mindful Moments, Stretch and Flex, and more!


![events_category_images_capture_the_flag[20] Capture The Flag](https://www.parsons.com/wp-content/uploads/bb-plugin/cache/events_category_images_capture_the_flag20-landscape-bc959f79375d7e4b64d47e1216d904d6-.jpg)