
Hosting a CTF: Part 6 – How To Create Solutions Slides Based Off Of Jeopardy-Style CTF Content
Now that we have read Part 1-5 let’s get to the final steps! First, we have to work through an example of creating solution slides based off Jeopardy-style CTF content using some of our questions from the last post. Using that same .pcap (or you can download our .pcap from <HERE> to work with), let’s build a detailed solution for the second question: 2. What is the first newsgroup that was subscribed to/accessed by the user in this .pcap?
I like my solutions to be rather complete, so a CTF newbie could read the challenge question and my solution and be able to solve the challenge without much trouble, so I tend to include both text and screenshots.
I started my solution by describing how to go about the question:
If you know what protocol newsgroups are run over, that makes this question easy. If not, you should Google “what Internet protocol do newsgroups run over,” and you’ll discover it’s NNTP (Network News Transport Protocol). So open up the .pcap in Wireshark, sort by protocol (by clicking the top of the “Protocol” column), and scroll down until you see a packet using NNTP. Right-click the first packet you see and click “Follow, then TCP Stream.”
I like inserting screenshots when the instructions are more than trivial, and I think this is a good place to add one.
Once you have the combined TCP traffic visible, scroll down to a line highlighted in red, as that’s a request the client sent to the server, and look for the first “GROUP X” reference, as that will show the user joining that group.
As shown in the image, I’ll edit the screenshot and circle the part of it the user needs to know to make it super clear.
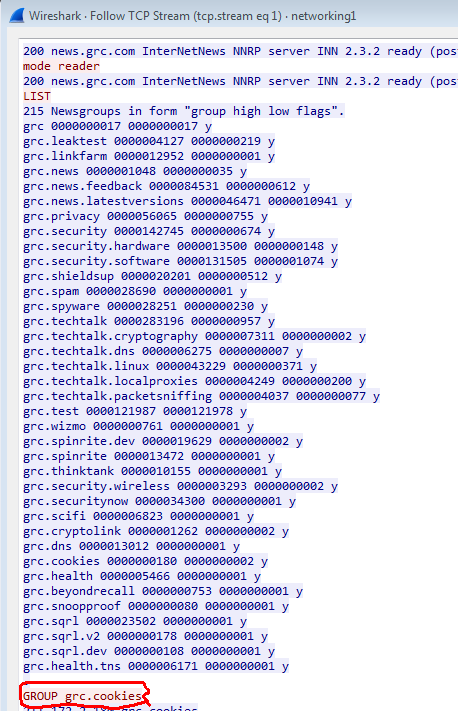
As shown in the attached picture, the user’s client issues the “GROUP grc.cookies” command, thus the grc.cookies group was the first news group that was subscribed to/accessed by the user in this .pcap.
I always state (and color code) the final solution to the challenge.
Now that we have the solution documented to that question, let’s add to it by answering the third question: 3. One of the messages read in the newsgroup talks about a popup alerting the user to a potential virus. What was the full name of that potential virus?
I recommend giving the solutions to participants afterward as a complete slide deck, so each question’s solution can build upon the others. For example, for this one you can start with:
Following the steps from the solution slide to the second question, you should be looking at the complete TCP stream based off the first NTTP packet seen in the .pcap. Keep scrolling down and look for a complete newsgroup message. Once you find it, keep reading until you see something about a popup and a virus detect. You can use the “Find” box at the bottom of the screen, if needed to help pinpoint its location (you can search for “popup” or “Virus” to help you look). You should see the text that says “Microsoft detected the Adware:Win32/RelatedLinks virus on your computer,” showing that Adware:Win32/RelatedLinks is the answer!
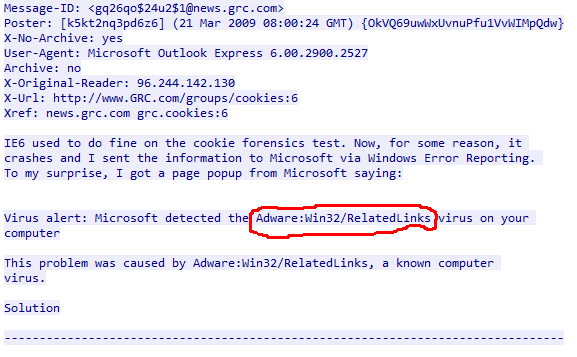
With the included image highlighting exactly wherein the message the potential virus name is found, you’ve given pretty clear instructions.
Now, the only thing left is to stand up your own CTF server for hosting the Jeopardy-style CTF! There are a plethora of options out there. We have experience with two for our CTFs. We first used PTCoreSec (https://github.com/PTCoreSec/CTF-Scoreboard), which we heavily modified, since the original is over seven years old now, and now we use CTFd, which has an amazing tutorial at https://github.com/CTFd/CTFd/wiki/Getting-Started to help you get started.